Zero Point Security’s Certified Red Team Operator (CRTO) Review and Retrospective
Taking a look at an alternative to the OSCP and PNTP
Ethics Disclaimers
First thing’s first, I must disclose that my employer purchased the course and lab time. The first exam attempt came bundled with the course. I paid for a second exam attempt out of my own pocket after failing my first. To the best of my knowledge I am the only person in the company I work for who has ever done business with Zero Point Security up until the point of my enrollment, and my employer and Zero Point Security have no other affiliations. Secondly, I took the exam in December 2021 and January-February of 2022. There have been changes that have been enacted since then, so my experience does not reflect the latest coursework and exam (If there have been any exam changes at all since I took the exam). As of date of publishing, I am not being compensated by Zero Point Security, RastaMouse, my employer, or anyone else for this post nor have I been up until point of publication. The content in this post outlines my thoughts and opinions, and mine alone.
Introduction
The Red Team Operator (RTO) course focuses attacking an Active Directory environment using Cobalt Strike, MSSQL Server abuse, AV evasion tactics, NTLM abuse, Kerberos abuse, enumeration techniques, and a little bit about the business side of things such as reporting, and requirements gathering. The exam is a CTF style exam giving you 48 hours of lab time over the course of 4 days, requiring 6/8 flags to pass. The labs and exam environments are hosted on Snaplabs.IO, which uses AWS as a backend. The lab and exam are also not internet connected, but access is given through a web browser via Apache Guacamole, with the ability to copy and paste in and out of the environment. The labs that accompany RTO are pre-loaded with various VMs that have everything you need to take the course including attacker tools, an AD environment, Cobalt Strike, detection tools, and then some. The course is administered through Thinkific. When I started the course, it was administered through Canvas, however while I was taking my second attempt at the exam it moved to the new platform.
Course Notes
Introductory materials
The course starts off with a general “What is this?” set of questions meant to clear up some terms about red teaming, OPSEC, how to plan for an engagement, types of engagements, and how to handle client data. I found this useful since I have no formal engagement experience, and knowing the administrative overhead on how to do an engagement safely, legally and most importantly, ethically is critical to obtaining and keeping trust with clients and staying out of jail. The next section of the course details some information on how you to use Cobalt Strike at a basic level and explaining how a C2 works. The end of the course includes report writing, data hunting techniques, and exfil techniques targeting anything from websites, to file shares. Depending on what the goals of an engagement are, the loot found may be the specified target. Otherwise this is absolutely something that should go into a report.
Goodies for defenders
Now, a little tangent. The way the course is structured after the first 2 sections is essentially a walkthrough of an engagement. It took me a embarrassingly long time for me to realize this, but it’s a great walkthrough that really helps cement a solid methodology. The course also covers detection using ELK stack, which is a cool feature to see from a defender’s perspective since you can see the detection methods from any account impersonation, Kerberos attacks or anything else that would set off Sysmon logs and use this to really know what defenders are going to be after. As someone with a little active defense experience from defense competitions, knowing the other side of an active attack and defense situation is extremely useful to keep in mind, and can really highlight and elevate skillsets that are needed to outperform the other side. I personally love that this aspect was touched on in RTO, and would like to see that in future courses I take.
Pwning the first box
RTO then covers some methods for external recon, as well as a few non-exploitative methods for initial compromise, meaning that there is no CVE exploitation to obtain the initial foothold. Instead the course focuses on abusing insecure features and misconfigurations rather than bugs. This is a common theme throughout the course. Once the first box is compromised, the course covers how to do host based recon, domain recon, privesc, and persistence. Seeing a non-exploitative way to get into the environment was interesting, however serves to restrict you primarily to brute force, credential stuffing, and phishing. This is not necessarily bad, it just limits initial attack vectors given the nature of the assessment.
Movin’ Movin’ Movin’
The course covers a significant amount of information on various lateral movement methods, primarily through misconfigured native windows features such as NTLM abuse, Kerberos abuse, or through common add-on programs for Windows (such as sysinternals), process injection, password cracking, and certificates (note ADCS abuse was not in the course when I took it, but has since been added). There is a heavy focus on Kerberos abuse to the point where it has it’s own chapter, as well as little tidbits thrown in many other chapters. RTO does a good job comparing and contrasting when certain abuses should be used, when they should be avoided, and the OPSEC considerations of different types of abuse. And as mentioned before, it continues to goes on to show how these attacks look from the defender’s standpoint so you can remain aware of what defenders are going to be looking for, or what their SIEMs are likely to be configured to alert against. Once again, I think this is brilliant. Defenders make better attackers, and attacker make better defenders. It’s a beautiful game of cat and mouse with one side always trying to 1-up the other.
All your domain are belong to me
Amongst the myriad of topics that are covered in here include: Pivoting, GPO Abuse, DACLS, Domain Trust abuses, MSSQL Server abuses, Skeleton Keys, Golden Tickets, pretty much anything you can use to work your way up the chain of users to a Domain Admin, and even shows ways to ensure domain-wide persistence alongside some of the potential long-term implications that this can cause with the client. Escalating privileges up to this point is not always needed during an engagement and that the principal of least privilege is still a good tenant to keep in mind during a red team exercise, knowing how to escalate is going to be something that just about every operator should know how to do for as long as Active Directory is being used in enterprise environments.
You didn’t see anything…
The last major category I want to point out is the course’s efforts to show you AV evasion. It’s focused on evading Microsoft Defender and other built in Windows defense mechanisms, and how you can customize and change Cobalt Strike’s payloads and C2 traffic to do so. It’s focused on the Artifact Kit, Resource Kit and the malleable C2 profile system that is available with Cobalt Strike. Note that these have been significantly changed in newer versions of Cobalt Strike, and seems to be part of the focus of RTO 2 (If that arrives 😉). I had no idea how AV evasion worked when I started the class, and I find it to be an interesting topic. I think highlighting it in a manner like this is a great idea and I will be continuing to look into this topic into the future.
Other thoughts
RTO is overall an excellent course that I am very glad I took. I strongly believe it will serve as the foundation of my future career as I continue to make the change from Vulnerability Management to Offensive Security Practitioner. There are a few minor criticisms that I have to make however, mostly focused on the Malleable C2 Profiles section of the course. While preparing for the exam I was reviewing this and found that the coursework was not sufficient for me to understand and crate my own profile. That being said, I found out later the intended design was to be using and modifying one of the sample C2 profiles, rather than building one from scratch. I’ll elaborate a little more on the exam under the “Exam Notes” section.
I also found the videos incredibly useful and I loved having them as options. I also like that the content in the videos is slightly different to the written content. I wish there were more videos in later sections of the course. Support for RTO is also available through both Zero Point Security’s website and Discord server. RastaMouse is very attentive at responding to requests within UK business hours and will normally address concerns incredibly quickly. That being said, if you are in need of help over a weekend or bank holiday, you will be waiting until UK business hours to receive a response as RastaMouse seemingly works completely on his own. Overall, I believe the course content is very strong and is a wholly worthwhile recommendation to anyone looking to jump into the Red Team space.
Labbing
As mentioned before, the labs are hosted through Snaplabs, which uses AWS as a backend. You will not have to supply your own AWS account to Snaplabs to use the platform, you just have to pay for more lab time on the Zero Point Security website. The exam is also hosted through Snaplabs. The labs that accompany the course are very well thought out and do an excellent job preparing for the exam. RastaMouse did an excellent job misconfiguring AD in these labs in such a manner to where they set up the perfect exploitation configurations, and allow you to practice all the concepts within the labs with minimal needless headache. Each machine, and the whole lab environment is also freely resettable so you can always reset if you manage to FUBAR something.
Creating an account and logging into Snaplabs will bring you to this dashboard. When starting, you will only see the lab field on the top left. The 2 exam fields will appear when you register for an exam attempt. 1 field will populate per exam attempt.
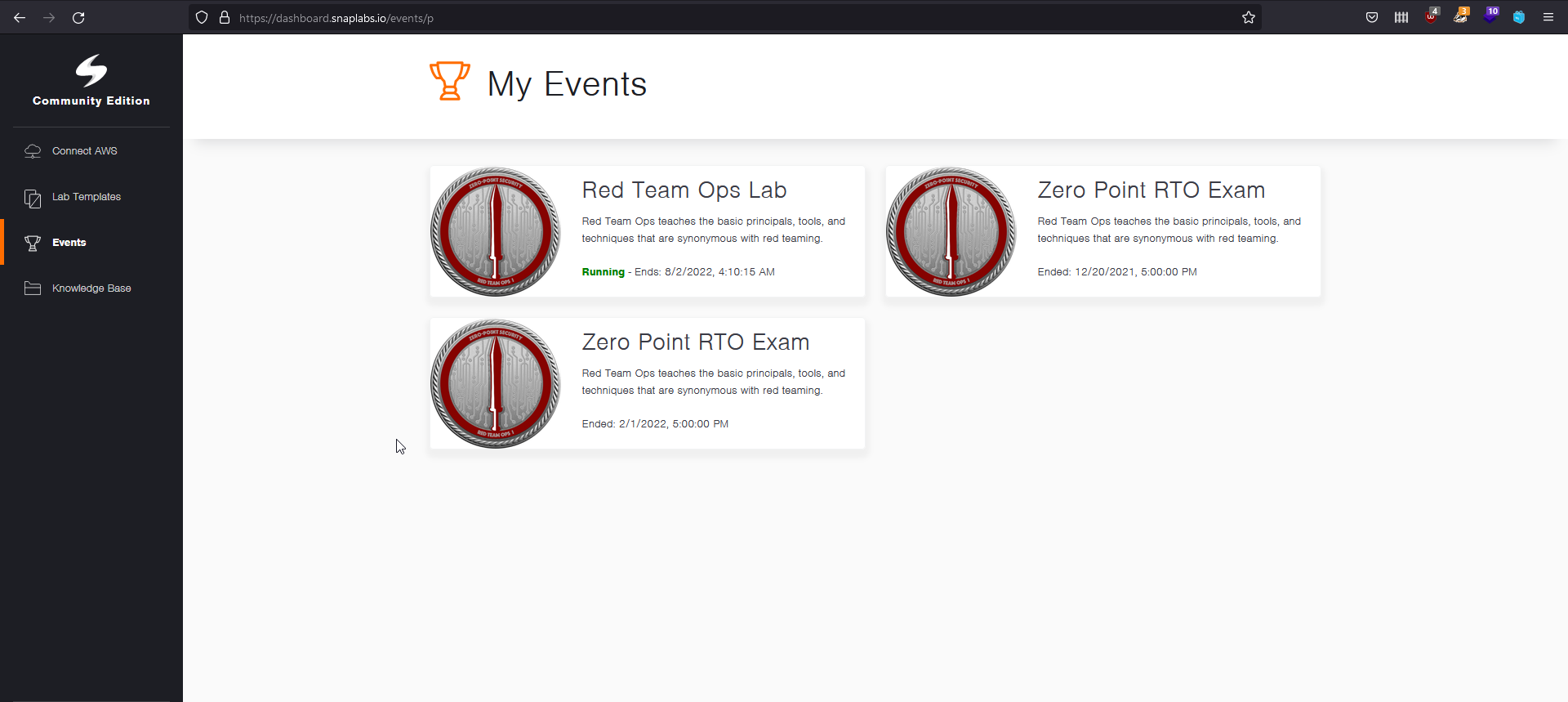
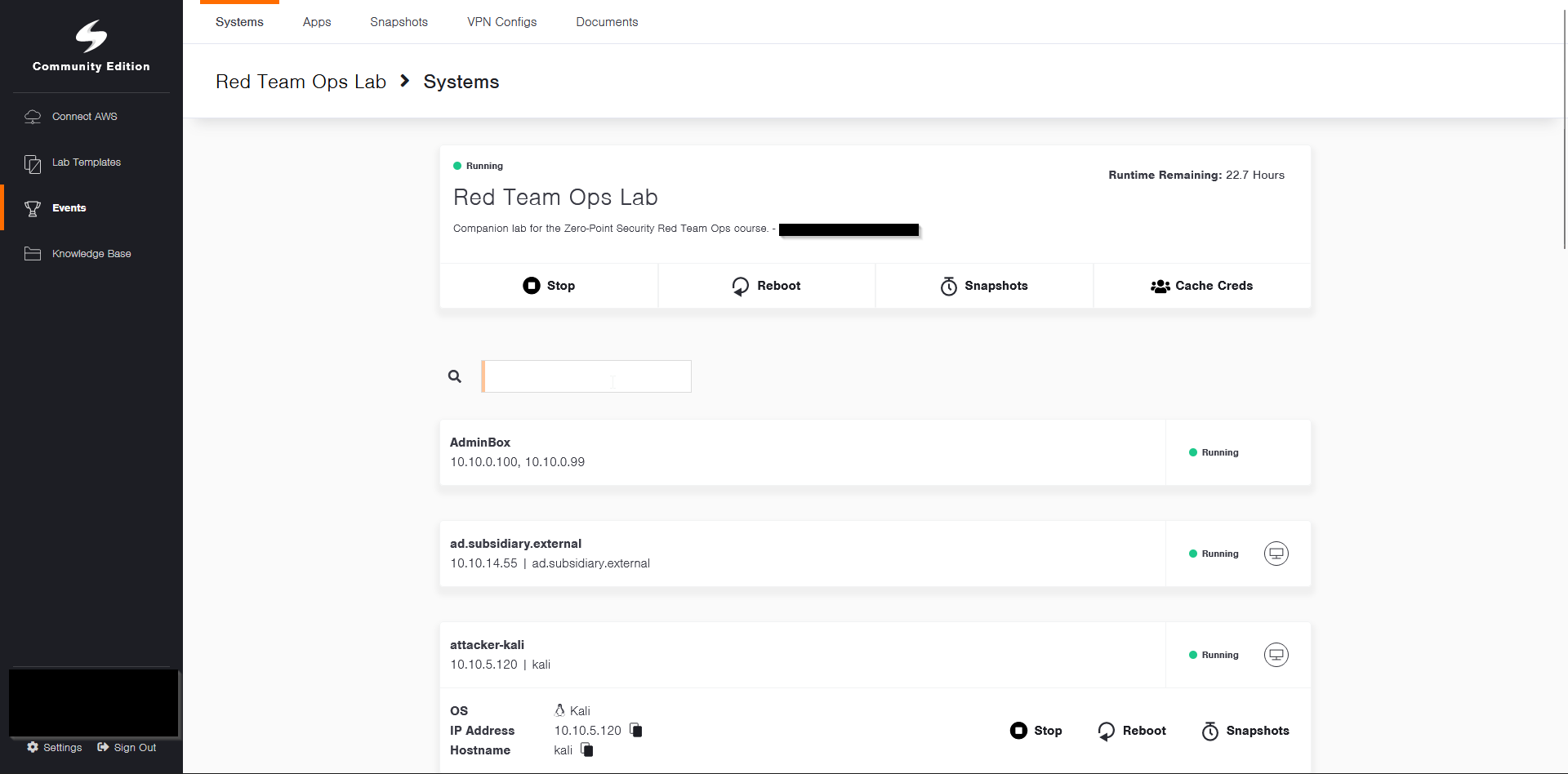
Once you click in to the labs, the initial landing page will have 18 machines shown on there, as well as a lab start button on the top. Each machine will have their hostnames and IP addresses shown on the cards. When clicking on the cards, you can also see the OS, button to copy fields to your clipboard, as well as machine controls like stop, reboot, and revert. Once the lab is booted up, give it about 5 minutes to finish loading up the guacamole session so you can access the machines.
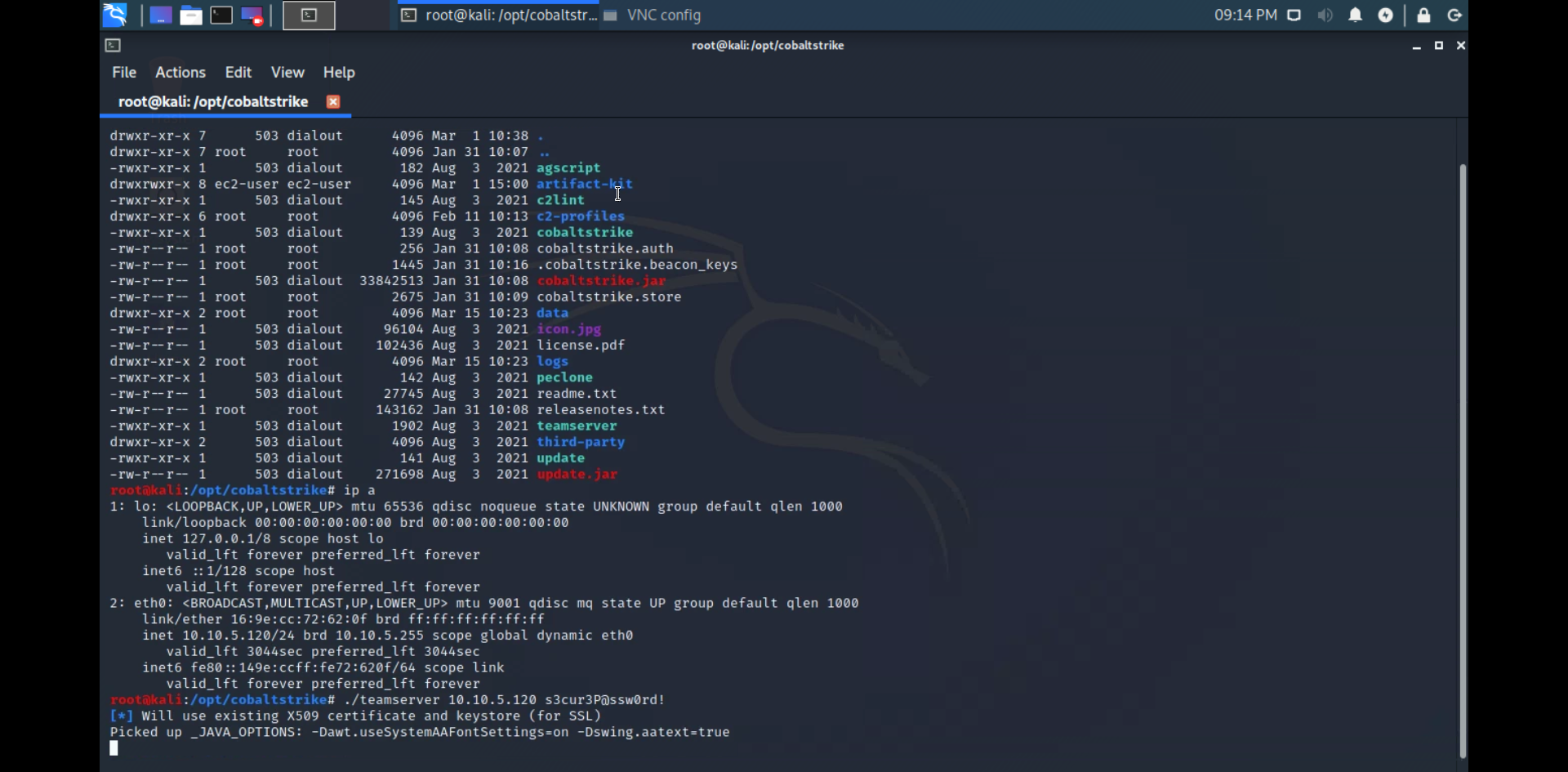
The interface once inside one of the VMs is pretty much like you would expect. A simple VM through a browser window. This was the first time I had ever heard of Apache Guacamole and I have to say, its pretty neat.
The labs are excellent and where the course truly shines. The best part about the Snaplabs experience is, every single student has their own lab environment. That’s right. You don't need Mike to attempt to spawn a shell, fuck a binary up, and have to revert the box causing you to lose your persistence. If you have to revert the box, its probably your fault. And if you have to revert the whole lab, it’s even more likely your fault. The lab time can be purchased for £1.25GBP an hour a la carte, so if you purchase the 40 hour bundle and find it isn't enough, you can always add more time. If I was purchasing the lab time out of pocket and not had my employer reimburse me, this is the way I would have done it as I have leftover lab time that is otherwise going to waste unless I get an itch to mess with Cobalt Strike again.
Exam Notes
The exam is a 4 day, 48 hours of lab time CTF style event where you have to obtain 6/8 flags to pass. Like the lab, it is hosted through Snaplabs, and includes a panel for you to submit your flags in. The exam is a fair representation and test of the knowledge and skills obtained in the course. I took the exam twice. The first time only capturing 1/8 flags, and the second time capturing 8/8 flags. The first attempt was marred by self caused problems, along with overreacting to said problems, then flailing around until I failed. I then took about a month to re-study on some weak points and prep kits and the C2 profile.
It was paced fairly well, and would push me to just the right point of frustration before I would capture the flag, get that dopamine hit and then go at it a few more hours. I passed the exam on the 30th of January, but still continued on after work on the 1st of February to get those last 2 flags. The machines used in the exam are similar to those in the labs, and utilizes the concepts presented in the course in interesting ways that follow the goals of the content, without allowing a straight copy paste, which is great. Exactly what I want to see in an exam.
Exam Tips
That being said, some things to do before having your exam. Now, I will not be going too in depth with tips since its well, an exam and I am not going to hand you a pass on a silver platter. However I am happy to provide some pointers from my experiences and pulling mostly from things RastaMouse has said so I do not get in any sort of trouble with spilling the beans.
- I actually highly recommend the Zero Point Security Discord. Its the easiest way to get a hold of RastaMouse if you need to. He and other members of the server give very good answers to course questions, and RastaMouse takes exam support requests over DM. The server also has pinned exam tips in some of the channels.
- After finishing the course work, spend time dialing in your C2 profile, Artifact Kit, and Resource Kit. You can take time before starting the exam to get a configuration working that works for you in the lab, then copy it out of the lab and get it into your notes. Screwing up the C2 profile is what killed my first exam attempt because some of my settings broke PowerShell in an impressive way. This happened when I got anxious, overcompensated to hell and back, and messed everything up. Keep calm and remember your training. Don’t be like me. Be better.
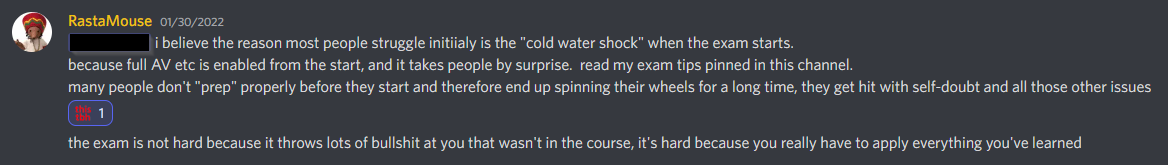
- The screenshot below was posted the day I passed the exam. Its 100% accurate. I did not prep well, and I suffered for it. If you prep, and can apply what you have learned, then you will do well on the exam.
Last Thoughts and Conclusions
Overall, I think the course, labs, and exam are excellent. They give students a wonderful foundation for future skill building and really reinforces the hacker mindset, while emphasizing differences between Red Teams and traditional Pentests. RTO in elaborates on the why and how in a manner that is practical, and useful. I strongly believe this course has set the foundations for the methodologies that I will use throughout my career. A huge thanks to RastaMouse for taking the time to create this course and for helping me figure out how I fucked up the first attempt. I have since purchased Offensive Driver Dev, and C2 Development in C#, and will make posts for those when I eventually make my way through them. (I have a bit of a backlog at the moment with learning C, and the Sektor7 Malware Development courses). I am impatiently awaiting RTO2 (Should it ever arrive, and not just be a troll) and will see if I can get enrolled once it’s released.
The link to the Red Team Operator course can be found here. And the FAQ here.