A Strange and Obsolete OSCP Review
Caught up in the middle of the transition, I can't actually tell you if the new course content is any good. I can tell about you what I experienced however, and that is exactly what I intend to do.
Ethics Disclaimers
Before we begin, I need to set some records straight and disclose a few things to you, the reader. First thing’s first, my employer purchased this course for me, like they did for my CRTO. I did not front this payment and get reimbursed like I did for the CRTL. Secondly after I posted my CRTL review, I have since been made a Moderator of the Zero Point Security Discord server. I had access to this course from February 19th, 2023 to May 18th, 2023. I took my first OSCP Exam attempt on May 18th, 2023 and the second on July 6th, 2023. As of the date of publishing, I am not, or have not received additional compensation for the purpose of taking this course, exam or writing this review by OffSec, my employer, or anyone else. The thoughts and opinions expressed herein are mine, and mine alone.
Why? - Background
Now. I want to make this painfully clear. I took the course material in the PEN-200-2022 version of the course and worked on the labs in the PEN-200-2023 (current, now just called PEN-200) version of the course, hence the title saying this review is already out of date. Because it is. OffSec has now taken the 2022 course off their website, so 2023 is the only version now. But, because I spent 5 months working on this, I have developed opinions and I am writing about them.
I have been a Tenable Monkey for the better part of 3 years now. My desire to get into an offensive security role is the major reason I have been taking these certifications over the last year and a half. I attempted a job search that was mostly a bust. I did get 1 offer from a local company (Thank you!), however the offer did not exactly line up with my goal of going offensive. So, I politely turned that offer down and chalked up the search to be a failure. There was one thing that kept biting me over and over when I interviewed with recruiters and managers: OSCP OSCP OSCP OSCP OSCP. I did not have one and apparently, even for Red Team roles it is a hard requirement at a lot of places. Apparently. Despite that I have 2 certs that are better suited. Anyways, that’s how I wound up here, and losing 5 months of spare time. I’m not bitter.
Diving into the course
As mentioned in the Ethics Disclaimer, I started this course on February 19th, 2023. This means that I was taking the PEN-200-2022 version of the coursework provided by OffSec. I was aiming for the following outcomes. First and foremost, getting certified so that when I go job hunting again after DEFCON 31 and hopefully find success this time around. The second thing I needed to do was address my deficiencies on some of the basics. Having taken some more advanced Red Team courses with no strong foundations, I had a weird balance of skills where I was missing some basic stuff, and I hoped to address that by tackling on this course.
Course Material
The 2022 course material is broken down in to 25 chapters. The ordering of them confused me slightly, which I will address here soon. I also quickly discovered that you can still download the PDF with the course content, which is great! Chapter 1 of the 2022 material is entirely admin information on the course itself. Covering things like how the learning management system is used, links to support documents, trying to prep your mindset to tackle the course, how to manage the 2022 lab, rules on lab use, and how exercises work. Then weirdly, a large block on reporting standards for the OSCP exam and a bunch of exam information. “Wouldn’t you want to put that at the end? You know, when students are actually prepping for the OSCP? Why would I need to know that right now?” were my thoughts upon first seeing it. Then even more confusing, the coursework mentions a report that you need to write for 10 bonus points on the OSCP, telling me that some exercises would be reported but others wouldn't. Okay?… But according to the FAQ (which of course, has now been changed with the 2023 course, so the old link is dead), I only needed to submit 80% of the flags obtained from each category in the exercises to obtain the points? So which one is it? I will come back to this later when I talk about course admin.
“Prerequisites”
With that in my mind, I started working on chapters 2-5, which I will collectively call “Prerequisites” Not exactly hacking material, but some legitimately useful stuff I have not been exposed to previously, like how find, cut, sed, nc, and other regularly used utilities I was just unfamiliar with (remember how I said I was lacking basics?). I think the 2022 material did a solid job pushing you to learn the strengths and weaknesses of how these utilities worked and what makes each useful, how to utilize them in BASH scripts, and other ways you can use these tools to accomplish your goals. To reinforce the groundwork laid out with the text and videos, The 2022 course has these little exercises that are essentially topical, hyper focused mini-CTFs. I loved these, at least in concept. They force you to learn how the utility works and provides that sweet, sweet dopamine hit when you capture that flag.
Information Gathering
The information gathering portion spanning chapters 6-8 of the 2022 course was fun. OffSec set up a few websites for you to enumerate and gather information against, to use in the exercises. They show some tools and services that you can use to assist in your adventures, how to do it manually, and overall nothing here speaks out as incredible, or bad, but it was good fun.
Piercing the Wall
The next part here is covering chapters 9, 13-15. These cover ways you can gain initial access, as well as various exploits, how to use them, and how to ensure they work properly. Fortunately, OffSec owns exploit-db.com. This means that just about every exploit they expect you to use are ones that are hosted on their platform, so you may not have to scour the internet for random PoCs. This section was interesting because it forces some interactions on how mail servers work under the hood, and various ways to execute payloads. As well as instructions on how to safely handle, and change exploits to fit your needs. The course content here was good, however the exercises here were terrible. I had loved the exercises up until this point, but some here were so finnicky and precise that half the challenge was trying to figure out exactly what OffSec was looking for, rather than making sure that I had the ideas down. A phishing challenge in particular is one that stands out as particularly nightmareish. I had spent a few hours doing it correctly in concept, but not formatted correctly for their automation to see the link and click on it. Of course, it was completely opaque as to what they wanted, as to try not to spoil the fun.
The 2022 course covers a small amount of Web Application exploitation as well. Specifically covering web application vulns that are easy to push to RCE. The course does a good job getting you introduced to Burpsuite, how to exploit some of the most common or dangerous vulnerabilities (from my limited understanding), explaining what they are useful for, and even how to remediate them in some cases. Web app is something I know I need to dig into farther, but I think that they did a good job at getting your feet wet here. There were some strange choices made on the order of exploiting some of these web app exercises, like including a SQLi challenge before introducing SQLi to the student, for instance. There is another issue later down the line of the course expecting you to know how to upgrade to a full TTY shell, before introducing it. Those were the 2 most annoying ones that continue to stand out to me, but I know there were other weird placement issues.
Post-Ex and Lateral Movement
Chapters 16-23 cover various post-ex and lateral movement activities. I don’t really have any strong feelings on the file transfers chapter, but man was I disappointed by the AV Evasion section. This was a key component of both CRTO and CRTL, and I was super interested in seeing OffSec’s take on it, which was some janky utility that was a pain to install and even worse to use. Now, I understand that the OSCP is not an evasion focused course, but I have no idea how any OSCP holder would come away being able to execute any payload even against a basic AV, which (I would think, and certainly hope) is something that would be ran into pretty regularly once an OSCP holder takes up Pentesting or god forbid Red Teaming as a job. I feel as though this is so basic that it needs to be covered at a surface level in OSCP, not a janky 10000 foot overview, not completely locked up in OSEP. Maybe this is just me discovering that I am more interested in Red Team, rather than Pen? Maybe. I don’t know. I am a Tenable Monkey hacker wannabe.
The privesc chapter was actually super helpful for me, because I was basically a 1-trick-pony for service executable privesc on Windows, and had no experience performing a privesc on Linux at all. I will say I came away happy with that chapter. The pivoting chapter in the OSCP also really strengthened a weak point of mine from both CRTO and CRTL, with the explanation given presenting it in a way where I was really able to grasp it. Especially covering how SOCKS proxies and SSH Tunnels are useful makes a ton more sense to me than it did from just taking the RTO courses.
The password attacks portion of the course was informative, if somewhat annoying. Annoying how? Well, in my case, I have a reasonably powerful GPU. Nothing too groundbreaking, just a Sapphire 6700xt, however the 2022 course really pushes you to use John the Ripper in the VM, which as you may know is a CPU based password cracker. Hashcat exists. Hashcat uses a GPU. Hashcat even has Windows and Linux binaries with (seemingly) the same syntax. So, why so much effort on John? My guess is that it’s because they can guarantee that everyone has a CPU, for obvious reasons. But I would think, that the GPU option should be shown off a bit more apart from saying “Hashcat exists, here you go” given that the venn-diagram between nerds running a dedicated GPU of any sort and nerds that are into pentesting enough to either pay $1600, or get someone else to pay $1600 for this course is probably nearly a circle. There was also a ton of effort put into wordlist generation, which was actually more interesting than I expected. Overall, I actually liked this portion of the course, and the exercises were pretty fun. I also want to dive a little deeper in password cracking methodology, as I find it interesting.
Finally we have AD. I was really looking forward to this, given again my previous training. It gave some older cmd based AD Enumeration TTPs that were cool to see. OffSec however decided that we should be writing our own PowerShell AD enumeration scripts rather than showing us how to enumerate it using excellent tools such as PowerView. Strange choice, but maybe they just wanted to show the power of PowerShell? On that note, those lessons really did give me a whole new appreciation of PowerShell’s abilities. Outside of that, most of what was covered here is covered in Zero Point’s RTO1 course, with more of a focus on Mimikatz, without Cobalt Strike. I came away from AD relatively happy, actually. I feel as though they did it justice without having to go off the deep end with it.
The last 2 chapters here were on a pair of C2 frameworks. Metasploit and Empire. I don’t have a ton to say about this part. I think it did a great job of exploring the differences between the C2 frameworks without beating it over your head. It really shows the pros and cons on how they work, how to use them proficiently and where to get help if required. It also increased my respect and fear of PowerShell. It really is a cool utility now that I have gotten to know some of it’s dirty secrets. One unexpected portion was covering how to write your own Metasploit module? It was certainly an interesting addition, but like, why was that included? Is that something that people regularly do? Why is that there? This is a legitimate question please email me if you know the answer.
BOF
Ah, buffer overflows. A topic I spent a LOT of time on. I did not forget about this and came back to this later in the course. After it was announced that they were no longer part of the exam, I was hoping to be able to ignore it and still get the 10 bonus points for completing 80% in each category by hoping that BOF would now be excluded, but I was wrong. Now, just so you are aware. I am TERRIBLE at BOFs. I have read how to do them in “Hacking: The Art of Exploitation”, did the TCM intro video on them on his Practical Ethical Hacking course, read them in the PEN-200 course, watched various YouTube videos on them. The PEN-200 telling of BOFs were the only ones that really made me really understand how they work in practice, not just theory. I don’t know if it was just repetition, or because the course showed it in a new light, but I finally got them figured out. Then I worked on the exercises. Holy hell, if I thought the phishing one was bad, that had nothing on these.
These exercises were absolutely miserable to do. They were so janky, and often crashed the container running the exercise, meaning that you had to revert the containers if the portion of the BOF it wanted you to do failed. Meaning that you had to spawn it, crash it, then wait 5 minutes to revert it, then repeat the cycle until you get it right. This was awful, and took up way too much time, especially for something that wasn’t even needed for the exam anymore. What’s more, is that one of the exercises wanted you to turn off ASLR on your own machine to perform. And the cherry on top here, is it does not tell you that in the course. I had to find that out after searching people’s complaining about that particular challenge in the OffSec Discord. Maybe someday I will learn exploit development, but today is not that day. This was a low point in the course, probably the worst part of it.
Remaining Pieces
The last portions of the course, chapter 24 and 25 cover a whole pentest against a small environment, and then some information about the labs. I don’t really have anything to talk about in here, as it was not anything particularly interesting. I still think the OSCP housekeeping should be here.
Videos
The last portion of the course content I want to discuss is the videos. They are remarkably okay. I have complaints, but they are manageable. The presenter is clearly using an old version of Kali. It did not really affect the function of the course material presented, but for $1600 I was expecting it to be on a version that was more modern. At least using their XFCE interface instead of an ancient GNOME one. Not trying to start a DE war here, so I want to clarify I am not calling GNOME outdated, but the interface they showed was simply an old GNOME version.
The presenter was nice and clear, however he talked incredibly slow. My guess here is that he was talking slow in order to accommodate for folks who don’t speak English as their first language. I want to be clear in that I have do not have a problem with that. I do however, have a problem with hiding the video playback speed interface on the main menu for videos, instead of on the pages that have the video player. I didn’t even know that was an option until I was halfway though the course and accidentally clicked on “videos” on the menu rather than within the text itself.
Wrapping up course content
Overall, I think the course content started off strong, but waned as time went on. The middle portion, specifically with exploits and the BOF sections were the most frustrating. And frankly, I don't really think there was a good reason for it. The challenges that were written for those sections were so janky, so needlessly specific, and so irritating that I nearly threw in the towel on even finishing them. The challenges were overall, a mixed bag. I again, love the idea of them, however they were a total crapshoot on whether they were good or not, I am not sure they were nearly as helpful as they could have been. Where I think the course stood out honestly, is showing you a solid methodology. It’s what I needed most, and still think I have room to grow here. However it covered those foundational things that I was missing and gave me an excellent platform in which I can grow.
For that, I am mostly pleased with the outcomes. I am however, extremely disappointed with the course administration and the in-course handling. Discrepancies like conflicting course material and FAQ entries, and having to go to support to clear these things up. For $1600, I was expecting that the course would be better put together than a $500 course run literally by a single dude. OffSec, for better for worse is a juggernaut in the training industry. The OSCP is the golden ticket to getting past HR for most offensive security roles in the US. I consider my feelings on the course to be very similar to my feelings about my post-secondary education. The start of it was great and I loved it. But then there were cracks, the cracks grew and grew, then by the end, I was mostly just trying to get it done. I think had I taken the 2023 version initially, I would have enjoyed it more. But the 2022 version was a mess, organizationally and administratively speaking and I left it with a bit of a sour taste in my mouth.
Wrenches
As mentioned at the beginning of this review, I was caught up in OffSec’s transitional period between their 2022 and 2023 curriculum. They initially had pretty aggressive timelines on getting the exercises done, but ended up pushing them out till the beginning of Q3 after community pushback. I think OffSec did a pretty good job with the initial community notification of the changes, however I think their update notifications were slightly lackluster. For instance, when OffSec changed the curriculum, they had a Discord notification, email blast, as well as FAQ pages that went up, and special Office Hours in their Discord server to address the changes. When they pushed out the exercises timeline however, that was not communicated particularly well. To the point of where I was trying to get the exercises done by April 18th, which was the original cut off date to be on the new curriculum, but found out from talking to other students that they pushed it back to the end of Q2 sometime in the first week of April. Fortunately, the changes really did not impact me super heavily due to my plans to have finished the 2022 material by April 18th anyways.
The biggest change was which lab I would end up attacking, and in this case that ended up being more a of boon than a bane. This change happened just before I hit the BOF sections of the course, which is partially why I initially skipped them and came back to them later. One thing that I think was handled well, was that I could download the course material again, so my saved copy was not just the older 2022 content, but also the new 2023 content. This is going to be useful for an ongoing project I have for overhauling my note taking efforts and structure of my notes.
Labs
This is where things get weird. So despite taking the 2022 course material, due to the shutdown of the monolithic labs of the 2022 course on April 18th, I had to attack the 2023 labs. These were significantly better than what I would have imagined the 2022 labs to be like. They switched from a monolithic lab that a lot of people have access to attack, to individualized labs that were (supposedly) significantly better. This came with the wrench for me however, in that there were much newer machines than the 2022 course content covered, so some privesc vectors did not end up working at all. Specifically which flavor of potato that was needed. There were also 6 total labs now. 3 that were mock labs of smaller companies, and 3 labs that mirror the OSCP exam structure.
The goal I set for myself to hit in the labs were to get the 30 proof.txt hashes required to obtain the bonus points on the OSCP exam. To do so, I intended to attack the Medtech, Relia, OSCP A, and OSCP B labs. Pwning these labs would have netted me 35 proof.txt hashes, sort of. So here is another example of that wonky course admin. The bonus point FAQ specifically calls out the need for 30 proof.txt hashes. However there are some machines that did not have proof.txt, and instead just had local.txt. Do these count? The answer turned out to be yes, but I found that out when messaging another student and they went and asked support when dealing with another manner. The way that FAQ should word the statement is “When the learning portal shows you have 30 machines in the course progress” as the criteria for the 10 bonus points. Anyways, back to the labs. Skylark was specifically called out in the course as one that goes above and beyond the OSCP exam, so I had no intention to handle that one. And OSCP C was skipped because I had my 30 and was just ready to be done.
The “business” labs were interesting. Usually a few standalone machines, and an AD network in them. Medtech was 10 boxes total, and Relia was 15. The single best part of these labs was pwning an AD section, getting DA and capturing 4 or 5 flags right away afterwards. Otherwise they introduced a bunch of exploits to run, and the community support was great at leading you towards tools that were required for the job. Some of what appeared in Medtech and Relia came back in the OSCP practice labs too, which was cool to see slightly different takes on them. I have relatively few complaints about the labs. The first is that the IP address you were assigned was not static and changed more often than not when connecting to the VPN again. This meant re-coding some tooling for the new IP if the exploit you used hardcoded the address and you didn’t change it to be a command line argument. The second is there were 2 Sundays I meant to take time to work on the labs and they were just down. Otherwise, apart from the time sink that Relia was for me, I do not have any other major complaints. They were way better than the course material. I just wish I had more time to tackle the labs. They were a great time.
Mildly Unhinged Rant Incoming - Slight Tangent
Herein comes probably my biggest complaint about course administration, the super misleading marketing about time you have to complete the course.
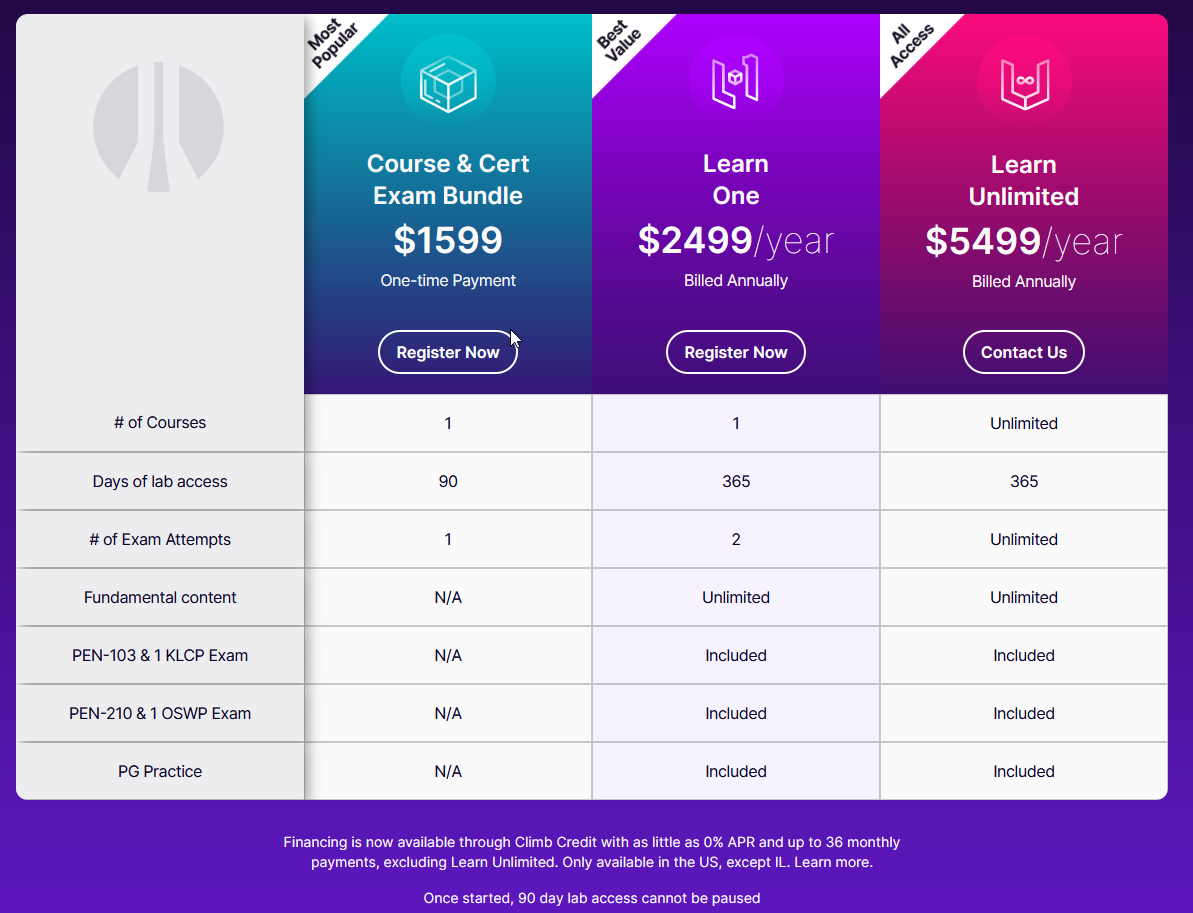
Do you see under “Course & Cert Exam Bundle?” where it says “days of lab access”? Do you see in the cell next to it? It says 90 right? That’s technically correct. You will have 90 days of access to the labs. Do you know what else you have 90 days to access? The course material. Do you know what happens after 90 days? They cut off your access to the course material. You can download the PDF if you want to use it like in ye olden days, however your learning portal access dies after 90 days, both material and lab. However. The course is designed to run through the labs after the course material. So, how I thought the course would go is that I would be able to work on the coursework at my own pace, then start lab access time when I was ready. NOPE. No, not at all. The way it actually works is that you have 90 days from your start time to get EVERYTHING done. This is why I disappeared for a little while, I just had way too much to do. I had to drop everything else I was doing to work on this. I spent 43 days out of my 90 in the course material, then spent the rest of the time in the labs.
Why is it like this? I cannot come up with a good reason why it’s this way. With either the old or new labs. The old ones were monolithic and constantly running, the new ones are launched on demand. So that’s out. Is it for load estimation? Support volume anticipation? I have no idea, however I think that OffSec needs to be way more clear on this being the case. It’s frankly ridiculous that they tout that the lab access is 90 days but I cannot find any references to the course material being 90 days. That needs to be called out somewhere on their website. Especially since unless you know all the OSCP content prior to taking the course, there is no way you’d actually have 90 days in the lab.
The second part of this rant, comes at the expense of their sales folks. Sales folks. I totally understand that you have a job to do, and quotas to meet. The following can be seen as a cautionary tale of what NOT to do when contacting me for sales. I will burn the bridge immediately if you do this. A week after exam attempt 1, I got a phone call from Washington D.C. on my personal phone. Like any other late Millennial or early Zoomer, I ignored it. Because I don’t know anyone in D.C. I then got a voicemail from the salesperson who said they worked for OffSec, and that they were the account manager for my company. They said they knew who I was due to some tracking in the OffSec website and that they knew I accessed the portal on my employer’s computer. They offered to set up some time to talk to me about course offerings.
I have many, many problems with this. First thing’s first. I don’t have a work phone. I am not in a 24/7 support team, so I am not provided one. I also provide a throwaway number to businesses because I don’t want my personal phone to be blown up all the time with thirsty sales calls. I am not exactly a fan of extensive web tracking and widespread surveillance. It’s why I don’t use Google Analytics for web traffic monitoring. I use Fathom Analytics. I don't need, or want per-user tracking. The second issue I have with this, is that I never gave OffSec my phone number. Which means they collected it through some 3rd party. I actually signed up for DeleteMe over this. Thirdly, they called me to sell me OSCP after I had already taken and failed it. That’s just the icing on the cake. Throwing ineptitude on top of blatant violations of my personal privacy. Sales folks, heed this warning. I will work with another salesperson in your company, or work with a different company if you ever do this to me.
A Note on Support
Support in the PEN-200 course was mostly handled through Discord, of all places. OffSec still has email and forum support, but I sent all my requests in through Discord, except for one. The first support request I had was that I had given OffSec an email alias that didn’t exist for my account. So I had to create that, and then have them re-send my welcome package. It also caused issues with my exam date, as I attempted to get to the email on that alias and it did not come through to my personal account, and I had to forward the exam start email to my personal inbox from my work email. The second issue I had with emails was changing my address off my work email, to a different personal email. However my work email was still receiving the exam start emails on my work email. I have no idea what’s wrong with that now, but there is something jank about it.
Back on topic, support was pretty good. They were easy to work with, clear in directions, and responsive. I am pretty happy with OffSec support. I have heard many horror stories about it, but in my experience they were amicable and I have no complaints on my end.
Exam
Attempt 1
I took my first crack at the OSCP on May 18th. I had my 10 bonus points from pwning 30 lab machines, and performing 80% of the exercises in each chapter. My strategy was to take on AD, plus a standlaone machine. I obtained a foothold on AD pretty quickly, then tried to privesc, which took a decent amount of time. Then the pivot to the second AD machine came quick, and then the privesc for DA stonewalled me. I lost about 6 hours on that and it caused me to fail my exam attempt. I managed to crack one of the standalones though, and perform the privesc there without major issues. I ended up only obtaining 30 points in total on the first attempt. 10 Bonus for completing the coursework, and 20 for rooting a standalone box. After consulting with some friends on whether or not it made sense to write the report, I was told not to bother since apparently, they don’t offer you any actionable feedback. So much for an org who wants to help students succeed.
Attempt 2
The second attempt was on July 6th, and I tried the same strategy. I never even got a foothold on the AD domain, but managed to root all 3 standalones for 60 points. Add the 10 bonus points, and that got me the 70 needed to pass. I was going at it from 0900 on July 6th, till 0300 on July 7th. After going to bed, then waking up around noon, I got to work on the report which I completed and submitted around 2200. Following that, I cracked open a victory beer and shortly afterwards, went to bed. I got an email around 0200 on July 13th stating that I passed the exam.
Final Thoughts
Overall, I have very conflicting thoughts on the OSCP. As mentioned before, I think of it like my degree in a lot of ways. For those who don’t know, I went to a fairly standard state university in a cyber program that was absolutely hell to make it through for a whole lot of reasons that I wont get too deep into here. If you see me with a beer at DEFCON I will happily rant about it. I had significant issues with the curriculum, even more with the administration, and the only reason I made it through was that I had a great support system of people who could help me when I was struggling. I did not enjoy going through the process much, but the results of that hard work paid off many times over already. For better or worse, the school can claim that they did their job because I was a good student who got a good job after graduating. At a high level, to a much lesser extent I had the same experience here. It plugged up some holes I had in previous training, I passed the exam, despite having some issues with the way the course was taught and administered, but I still achieved OffSec’s stated outcomes of achieving my OSCP and hopefully can put it to good use soon. By their definitions I am a success case, even if I’m not too impressed by the process.
Do I recommend it?
This gets really tricky because there are a ton of variables. First things first, I did not take the current coursework. So no matter what I recommend, it’s not informed to the current standards of the course. I think this question is going to be a highly specific answer heavily dependent on whoever is asking. Are you trying to break into an offensive role and have been stonewalled? It might make sense to take it assuming that companies aren’t looking at alternatives like PNTP, CRTO, or CPTS. If you’ve been working in an offensive capacity for any longer than 3-6 months, and are confident in your ability to continue to learn and grow, don’t bother. Work on some independent learning or something more advanced. Your experience should get you in the door somewhere else anyways. Do you have known weak points with the basics and you don’t know what questions to ask to get some improvement? Then it might make some sense to take it.
Unfortunately, in the US the OSCP reigns supreme in it’s dominance within the hiring space. In my experiences, there are a significant number of places who will not even consider you without it, even if you have certifications that are more in line with the role (looking at you, companies who passed me up for Red Team roles because I did not have OSCP). I sincerely hope that the industry opens up to alternatives to continue to give OffSec a run for their money. Competition is good. The more the merrier. For now, I cannot give a blanket recommendation of the OSCP. I think that it should only be taken if you have to. The course is expensive, and there are far cheaper options that do a great job of filling a similar role of getting you ready for a career in pentesting. I intensely dislike how hard it is to get actionable feedback out of OffSec. If I can get some feedback directly from training institutions on what I need to improve next time around so I know what to work on, that is vastly preferable to me than the “Figure out what went wrong” mentality that OffSec uses.
Changelog
2024-09-17: Redacted old username.